With the launch of Sophos high-availability firewalls on AWS Marketplace, we look at the differences between high availability and fault tolerance.
When it comes to dealing with cloud computing infrastructure, it’s important to identify how high availability (HA) and fault tolerance (FT) differ from one another.
The good news is that Sophos Firewall is now available as an HA/FT deployment solution in AWS marketplace. Check out the following links to learn more:
Sophos Firewall high availability deployment | Sophos Firewall fault tolerance (AA) deployment
High availability
Let’s use some non-IT analogies here, first to explain high availability – also known as active-passive, also known as active-standby mode.

Here we have the infamous double-neck guitar, built for epic guitar solos. If one of these guitar’s strings break in the middle of a performance, the guitarist would quickly shift over to the other guitar, continuing to play music so fans don’t miss their favorite song.
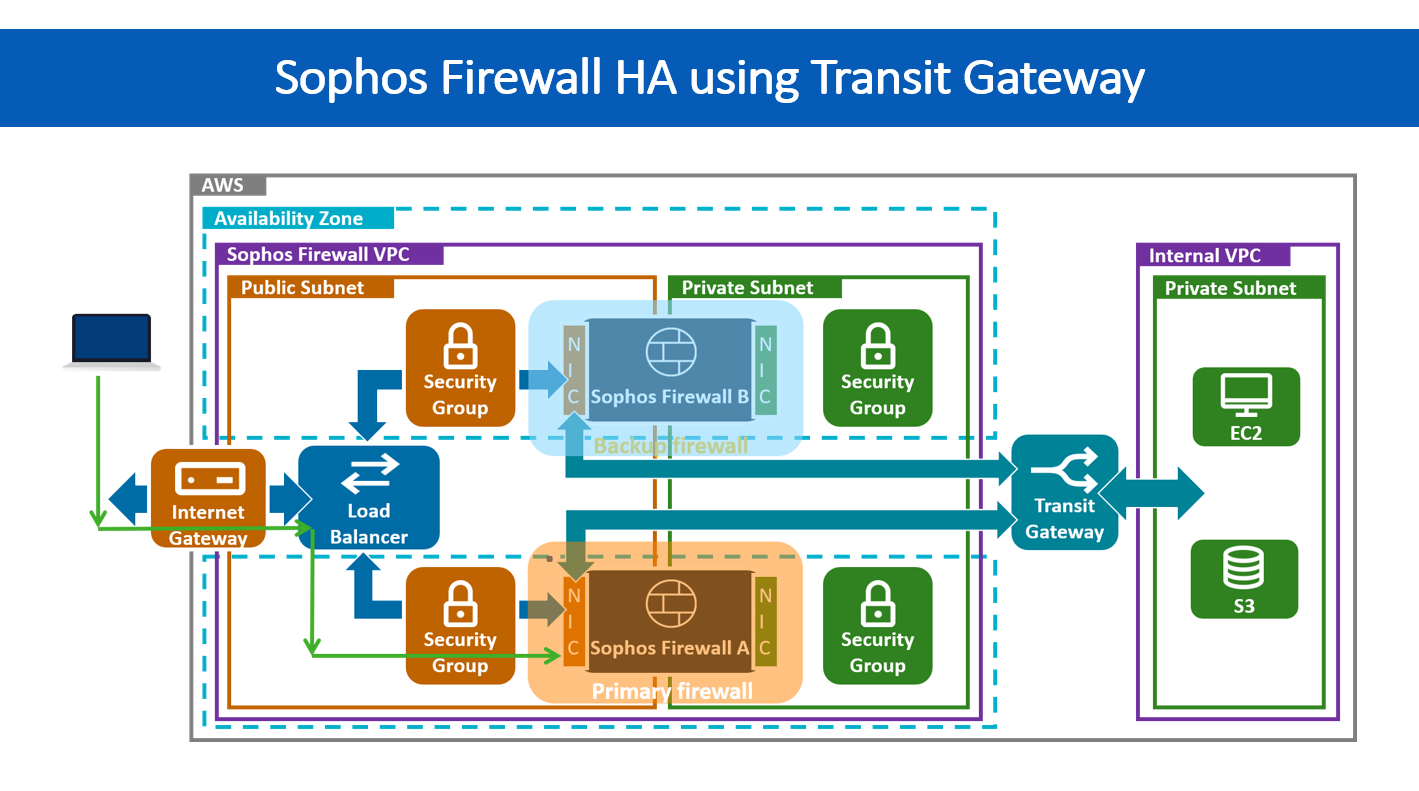
From a cloud infrastructure perspective, here’s a network diagram showing the logic of high availability.
Two firewall nodes are deployed in an AWS account to achieve redundancy. As you can see, Sophos Firewall A acts as a primary device, processing all the traffic.
Sophos Firewall B is also connected to the load balancer. However, it acts as a standby/backup device. It will only start processing the traffic if Sophos Firewall A is offline for some reason.
As the traffic fails over from the primary firewall to the backup one, we’d expect only minimal downtime/network disruption – perhaps just a few seconds. This logic works the same way for both inbound and outbound traffic.
Fault tolerance
As for fault tolerance, let’s stick with another non-IT, rock-themed analogy.

In this image, we have two guitarists, both playing for the crowd. If one guitarist breaks a string or smashes his guitar, his bandmate carries on playing and the audience never misses a thing.
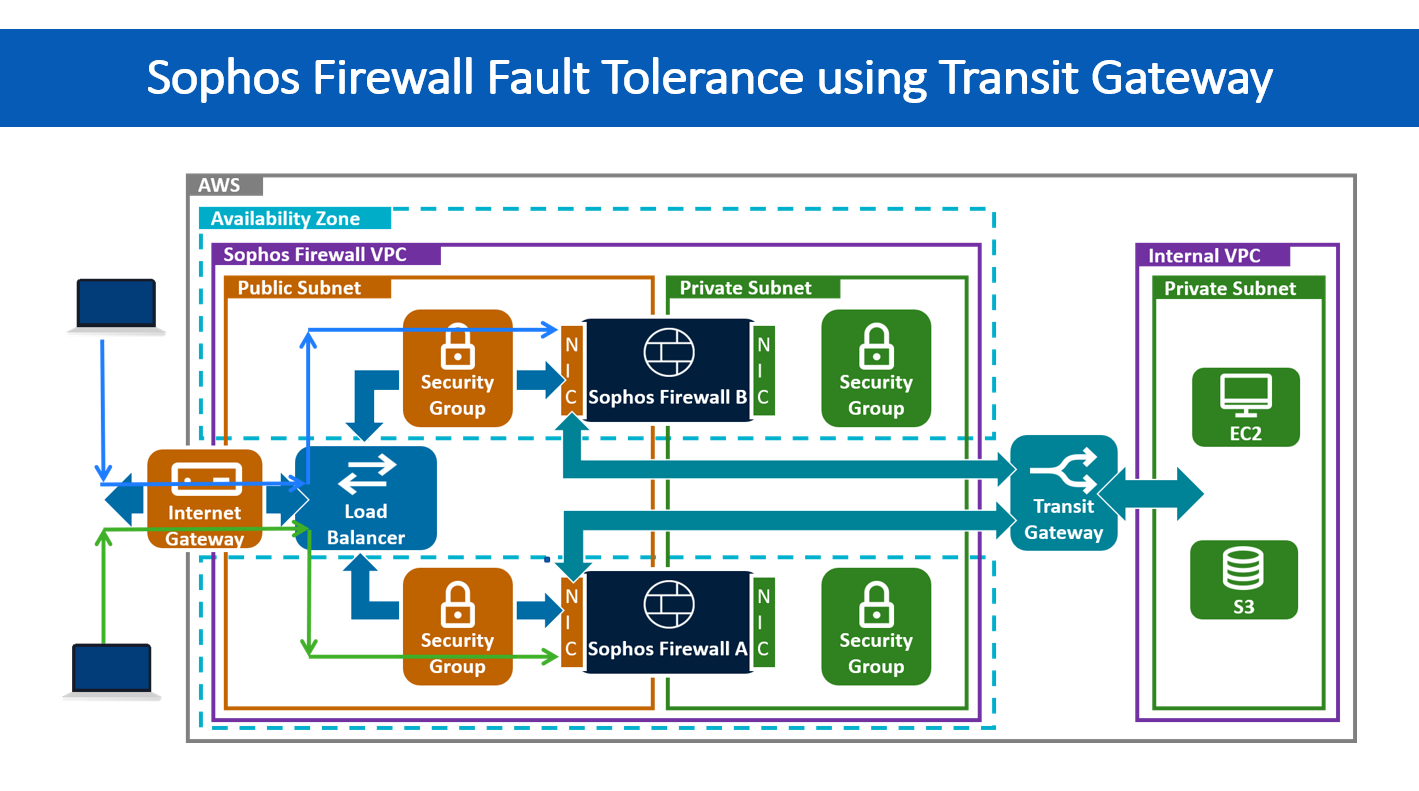
And again, from a cloud infrastructure perspective, here’s a network diagram showing the logic of fault tolerance.
Two firewall nodes are deployed in an AWS account to achieve redundancy. In this deployment scenario, there is no such concept of primary-backup firewalls.
Both Sophos Firewall A and Sophos Firewall B would equally process inbound and outbound traffic. In a worst-case scenario, if one of the two firewalls goes offline, there wouldn’t be any downtime since traffic would still be processed by the other firewall until the offline firewall is replaced. So, this gives us zero downtime in a true sense.